Rate Limiting Rules
Response: Rate Limiting¶
Advanced Rate Limiting
Matching Criteria:
- Define the traffic scope for rate limiting rules
- Specify the matching and counting criteria for rate limiting
- Define frequency, action, and duration
Counting Criteria:
● Independent IP
● Request headers
● Cookie
● Query parameters
● URI
● Country/Region
● X-Forwarded-For
● Request source
● User-Agent
● Referer

Response: Rate Limit Rules¶
Menu Path: "Plan List -> Configuration Policy -> Policy Group -> Rate Limit Rules"
Protect Origin Server: High-precision DDoS protection to shield origin servers from excessive requests
Protect Customer Data: Safeguard sensitive customer information against brute-force login attacks
Protect APIs: Set API usage limits to ensure availability and prevent abuse
Cost Savings: Define thresholds to allow only legitimate traffic, avoiding unpredictable costs from traffic spikes or attacks


Response: Example: Granular Protection for Web Traffic¶
All firewall rule fields can be matched, such as:
● Request path and method
● Country/Region
● Dynamic fields (e.g., bot score)
● Exclude IPs in whitelists
● Request headers and all HTTP fields
Counting Criteria
● Independent IP
● Country
Time Frequency
● 1 second
Policy
● Block requests exceeding the rate limit

Response: Example: Preventing Data Scraping and Leaks¶
Common Scenarios
● E-commerce: Bots scraping price data or automated purchases
● Aviation: Scraping passenger info or booking codes
● Distributed bots using identical session IDs for requests
GET https://api.store.com/lookupprice?product=3ds5tg
Accept: application/json
Cookie: session_id=12345

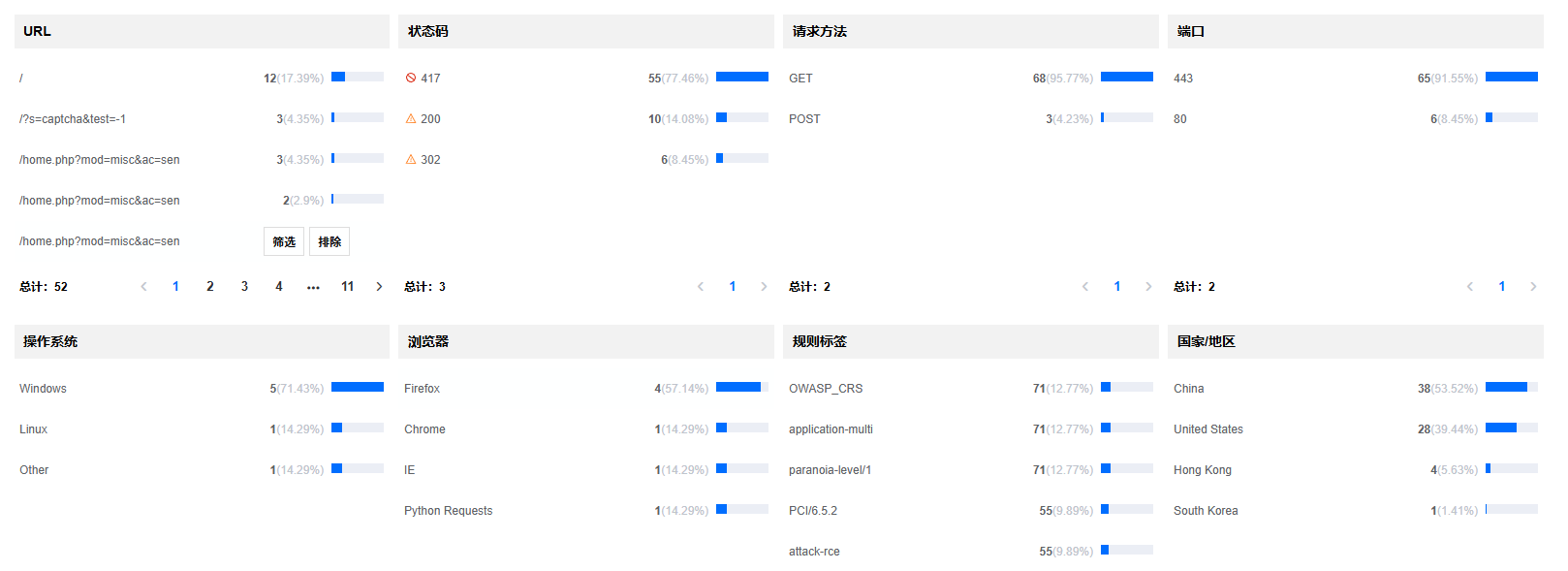
Recovery: Review and Refine Rules Step-by-Step¶
● Optimize rules with data insights
● Adjust rate limit thresholds
● Review attacked rules, fine-tune thresholds, and keep them enabled
● Analyze attack IPs or logs to determine if List-based blocking should be enabled to reduce risks
● Evaluate if other configurations need optimization
● Optimize caching rules for static resources
● Update TLS versions or configure HTTPS redirects