Super WAF3.0 (Security Operations PDRR Model)
WAF Product Definition¶
●WAF (Web Application Firewall) helps protect web applications by filtering and monitoring HTTP traffic between web applications and the internet. It typically safeguards web applications against cross-site forgery, cross-site scripting (XSS), file inclusion, SQL injection, and other attacks.
●WAF operates as a Layer 7 defense strategy (in the OSI model) and does not protect against all types of attacks. This attack mitigation method is usually part of a suite of tools that collectively establish comprehensive defenses against a range of attack vectors.
●By deploying a WAF in front of a web application, a barrier is created between the web application and the internet. While proxy servers protect client identities through intermediaries, a WAF acts as a reverse proxy, directing clients through the WAF to reach the server, thereby preventing server exposure.
●WAF operates through a set of rules commonly referred to as "policies." These policies are designed to filter malicious traffic and protect against application vulnerabilities. Part of the WAF's value lies in its ability to quickly and easily modify policies, enabling faster responses to different attack methods. During CC attacks, rate limiting can be swiftly implemented by adjusting WAF policies.
Core Value: Provide users with precise web application protection and ensure business continuity
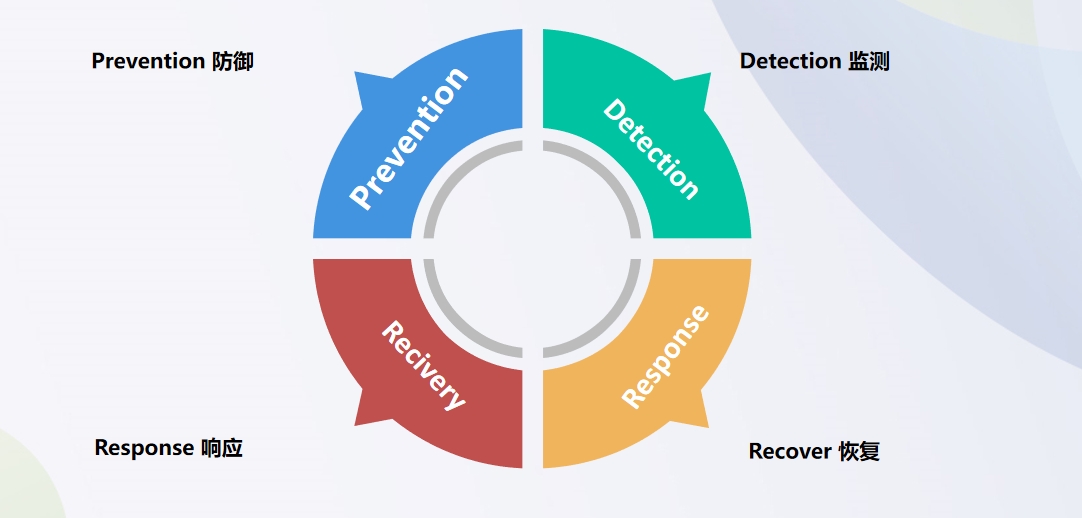
Customer Expectations for WAF - Operational Security PDRR Model¶
Global Network Architecture and Principles¶

Globally Distributed WAF Nodes (International Anycast + Domestic China Nodes + CN2 Return Optimization Nodes)
WAF System Architecture¶

Web Application Traffic
Defense: Basic Protection Setup – Switch CNAME Resolution for Immediate Effect¶


**Before Integration**: Without our service, the origin server is exposed to the public internet.
**After Integration**: With our service, all requests are routed through Anycast to the nearest protective node data center, processed, and then forwarded to the origin server.

Monitoring: Data Collection and DDOS Attack Traffic Analysis¶
Utilize the User Security Center - Security Acceleration to analyze traffic patterns, understand legitimate user behavior characteristics, and review firewall security events.


Monitoring: Data Collection and Layer 7 WEB Attack Traffic Analysis¶
Utilize the User Security Center - Web Application Firewall 3.0 to analyze traffic patterns, understand legitimate user behavior characteristics, and review firewall security events.


Response: Protection Mode – Log Only¶
Menu "Plan List -> Configure Policy -> Select the Corresponding WAF Rule Name in the Policy Group"
Enable log-only mode for pre-testing to identify potential vulnerabilities and fix them. No interception actions will occur during this process.

View detailed data in the log service and preemptively add whitelist entries with one click.

Response: Protection Mode – Enable¶
● Menu "Plan List -> Configure Policy -> Select the Corresponding WAF Rule Name in the Policy Group"
**Interception mode enabled**. For custom rules, rate-limiting rules, managed rules, configured conditional policies, and **OWASP** rule sets, interception actions will be triggered for matching policies.


View detailed data in the log service and preemptively add whitelist entries with one click.

Response: Custom Rules¶
Menu "Plan List -> Configure Policy -> Policy Group -> Custom Rules"
Advanced Edition Custom Rules
Matching Criteria:
● Independent IP
● Hostname
● Request Headers
● Cookie
● Query Parameters
● URI
● Country/Region
● X-Forwarded-For
● Request Source/Request Headers
● UA
● Referer
Actions:
● Skip Rule
● Log Only
● Intercept
● Whitelist Rule ID

Response: Rate Limiting¶
Advanced Edition Rate Limiting
Matching Criteria:
- Define the traffic scope for rate-limiting rules.
- Specify the matching and counting criteria for rate limiting.
- Define the frequency, action, and duration.
Counting Criteria:
● Independent IP
● Request Headers
● Cookie
● Query Parameters
● URI
● Country/Region
● X-Forwarded-For
● Request Source
● UA
● Referer

Response: Rate-Limiting Rules¶
Menu "Plan List -> Configure Policy -> Policy Group -> Rate-Limiting Rules"
Protect Origin Server: High-precision DoS protection to shield the origin server from excessive requests.
Protect Customer Data: Safeguard sensitive customer information from brute-force login attacks.
Protect APIs: Set API usage limits to ensure availability and prevent abuse.
**Cost Savings**: Set thresholds to allow only legitimate traffic, avoiding unpredictable costs due to traffic spikes or attacks.


Response: Policy Group -> OWASP Managed Rule Sets¶
SQL Injection (SQLi): Block SQL injection
Cross Site Scripting (XSS): Block cross-site scripting attacks
Local File Inclusion (LFI): Block attacks exploiting local file inclusion vulnerabilities
Remote File Inclusion (RFI): Block attacks exploiting remote file inclusion vulnerabilities
Remote Code Execution (RCE): Block attacks exploiting remote command execution vulnerabilities
PHP Code Injection: Block PHP code injection
HTTP Protocol Violations: Block malicious access violating HTTP protocols
HTTPoxy: Block attacks exploiting remote proxy infection vulnerabilities
Shellshock: Block attacks exploiting Shellshock vulnerabilities
Session Fixation: Block attacks exploiting fixed session IDs
Scanner Detection: Block hacker scans on websites
Metadata/Error Leakages: Block source code/error information leaks
Project Honey Pot Blacklist: Honeypot project blacklist
GeoIP Country Blocking: Block IPs based on geographic location
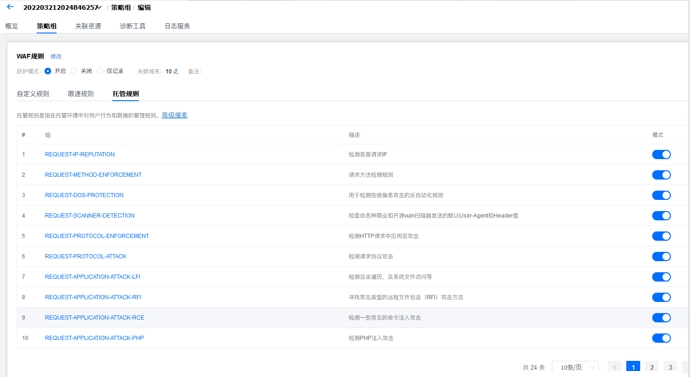

Recovery: One-Click Whitelisting¶
View logs and add whitelist entries with one click: **Web Application Firewall 3.0 -> Log Service – Click or search for the relevant log ID**.

Recovery: Skip via Custom Rules¶
**Web Application Firewall 3.0 -> Plan List -> Policy Group -> Custom Rules -> Add Rule**. Skip the three major rule sets here.

Recovery: Disable Granular Managed Rule Entries via Managed Rules¶
**Web Application Firewall 3.0 -> Plan List -> Policy Group -> Managed Rules -> Advanced Search**. Disable granular rules here.

Recovery: Review and Gradually Improve Rules¶
● Refine rules based on data analysis
● Adjust thresholds for rate-limiting rules
● Review attacked rules, adjust thresholds, and keep them enabled by default
● Review attack IPs or analyze logs to determine if List-based blocking should be enabled to reduce risks
● Optimize other configurations if needed
● Optimize caching rules for static resources
● Update TLS versions or configure HTTPS redirects
