Upload Certificate
If your origin server has domains configured with certificates, please review the following content first.
Recommendation: Use the Certificate Hosting Upload Method¶
Hosted Certificates¶
Click to upload a certificate

Select SSL Certificate Hosting → Upload Certificate

Paste the certificate content and save to complete the upload

After successful upload, you can view the domain, brand, expiration time, and status

About HTTP Certificates:¶
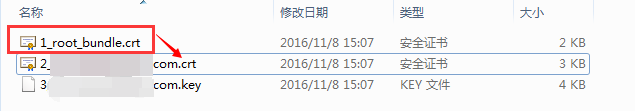
CA institutions typically provide certificates in the following formats. Cloud Protection uses the Nginx version with RSA algorithm:

Navigate to the Nginx folder, open the ".crt" (certificate) and ".key" (private key) files with a text editor to view the PEM-formatted certificate content and private key:
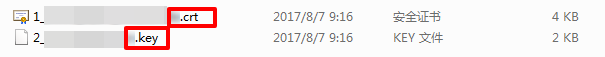
Certificate¶
Certificate extensions are usually ".pem", ".crt", or ".cer". Open the certificate file in a text editor to see content similar to the format below. PEM format: Begins with "-----BEGIN CERTIFICATE-----" and ends with "-----END CERTIFICATE-----". The middle content has 64 characters per line, except the last line which may be shorter:
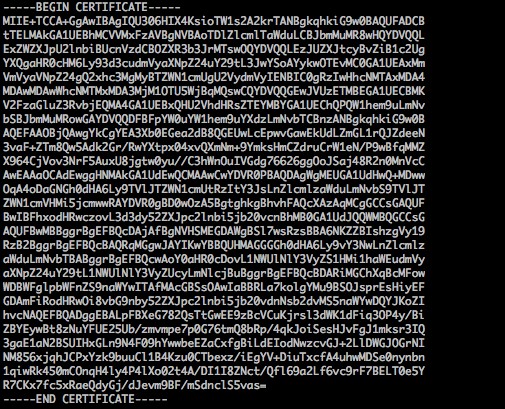
For certificates issued by intermediate CAs, your certificate file may contain multiple certificates. You need to manually concatenate the server certificate and intermediate certificates when uploading. The rule is: server certificate first, followed by intermediate certificates, with no blank lines in between. Usually, the issuing CA provides instructions - please check their documentation.
Note: No blank lines between certificates Each certificate must be in PEM format
The format for certificates issued by intermediate CAs is as follows:
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
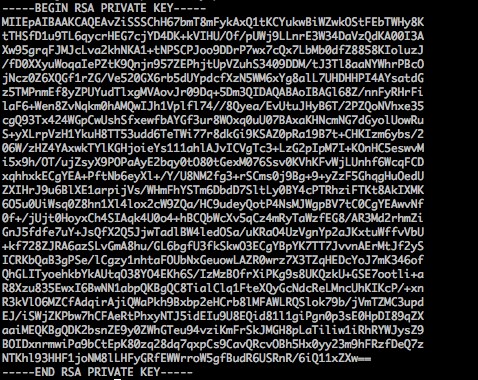
Private Key¶
Private key extensions are usually ".pem" or ".key". Open the private key file in a text editor to see content similar to the format below. PEM format: Begins with "-----BEGIN RSA PRIVATE KEY-----" and ends with "-----END RSA PRIVATE KEY-----". The middle content has 64 characters per line, except the last line which may be shorter.
If your private key begins with "-----BEGIN PRIVATE KEY-----" and ends with "-----END PRIVATE KEY-----", we recommend converting the format using openssl with this command: openssl rsa -in old_server_key.pem -out new_server_key.pem
Format Conversion¶
Currently, Cloud Protection only supports PEM format certificates. Certificates in other formats need to be converted to PEM, preferably using openssl. Below are conversion methods for several popular formats: DER to PEM DER format is commonly found in Java platforms. Certificate conversion: openssl x509 -inform der -in certificate.cer -out certificate.pem
Private key conversion: openssl rsa -inform DER -outform PEM -in privatekey.der -out privatekey.pem
P7B to PEM P7B format is commonly found in Windows Server and Tomcat. Certificate conversion: openssl pkcs7 -print_certs -in incertificat.p7b -out outcertificate.cer
Open outcertificat.cer with a text editor to view PEM-formatted content. Private key conversion: Private keys can usually be exported from IIS servers. PFX to PEM PFX format is commonly found in Windows Server. Certificate conversion: openssl pkcs12 -in certname.pfx -nokeys -out cert.pem
Private key conversion: openssl pkcs12 -in certname.pfx -nocerts -out key.pem -nodes
Certificate Chain Completion¶
When configuring with your own certificates, you might encounter incomplete certificate chains. You can complete the chain by appending the CA's certificate (PEM format) content to the end of your domain certificate (PEM format). Alternatively, contact our technical support for assistance.